RaySecur’s Director of Mail Security provides a training webinar discussing the implementation of a mail security program.
In this webinar, views will learn how to design and implement a mailroom security program, and develop standardized operating procedures for mail screening.
Take the PDF with you ↓

About Cody Martin
Cody Martin had over 12 years of experience as a Federal Agent with the U.S. Postal Inspection Service, and several additional years as a mail security consultant.
He has worked on mail security for a Super Bowl, with the Secret Service for President George W. Bush in retirement, and has investigated hundreds of mail threats.
Implementing a Mail Security Program
What makes a mail security "program?"
A mailroom security program is a component of physical security used to prevent or minimize the introduction of threats via the mail stream.
It provides a systematic approach to protect people and assets from the point of acceptance through the final delivery or destruction of the mail piece.
When effectively implemented, it closes a gap often found in physical security programs.
Why does it matter?
Mail security is a critical vulnerability, and an often unaddressed security gap, for major companies, prominent individuals, governments, and others.
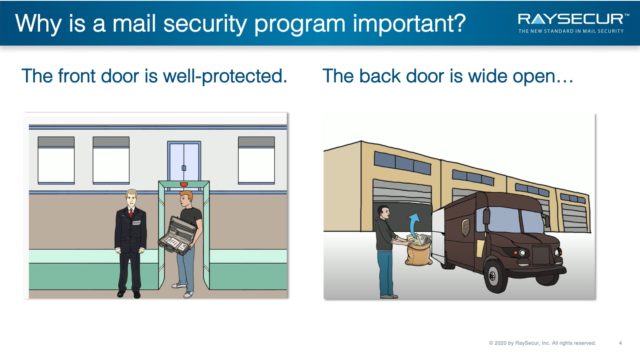
The front door of most corporate office buildings, data centers, financial institutions, or pharmaceutical manufacturers are often well secured.
Security cameras, security checkpoints, identification protocols, controlled access points, etc., are all part of a physical security plan.
In contrast, someone can drop a letter or small package into an anonymous USPS collection box, which often enters through a back door or loading dock bypassing all of those security measures.
One third of major corporations report receiving mail-borne threats annually, and many receive more than one.
Revenge from employees, former employees, and other stakeholders is the most common motive, according to a recent US Postal Inspection Service (USPIS) report.
With three simultaneous crises—public health, economic, and social justice—security teams are facing even greater challenges.
More common than you think.
1 in 3 Fortune 500 companies receive at least one mail threat per year.*
2019 Industry Mail Security Survey
- 34% of surveyed companies had at least one mail threat detected in the previous year
- 16% had more than 3 threats in that same time period
- Threatening letters doubled
- Drugs and illegal substances quadrupled
You can see by the numbers above, the odds of being targeting by a mail related threat are greater than you may think.
The big takeaway here is the increase in threatening letters, which has doubled over the last year, and the fact that drugs and illegals substances have quadrupled during the same time frame.
* Government Technology & Services Coalition, “Third of Companies Got Mail Threats in Past Year While Biological Screening Doubled,” May 19, 2019
10 incidents per day — that we know of
You may notice discrepancies in reported incident numbers.
Keep in mind that many incidents are not reported or are underreported based on agency requirements and classification standards.
USPIS 2019 Annual Report
- Dangerous Mail Investigations (DMI) Unit
- 400 specially-trained inspectors
3,289 suspicious incidents (powders, liquids) - 125,000 suspicious mail items subject to forensics exam
US Bomb Data Center
- 7,404 suspicious packages in 2018
- 2,261 incidents involving letters or parcels
What we do know is that the numbers are high and we are seeing large increases in certain areas.
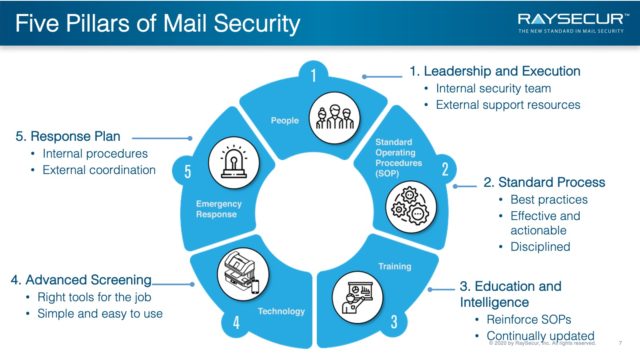
Five Pillars of Mail Security
All five are required
While every person, package, and backpack coming in the front door of a major company is typically checked, most at the ‘back door’ of a mailroom are not.
When a mailroom security program is lacking, the back door is left wide open.
If mail pieces enter your location unscreened, standard security measures are bypassed, and critical infrastructure is exposed.
When personnel, SOPs, training, technology, and emergency response come together, organizations can strengthen their security against mail-borne threats.

Pillar #1 — People
The first pillar is, which we split into internal teams and external teams.
Internal teams consists of everyone from the front-line worker to the top-level executive.
External teams are the folks you partner with outside your organization who provide expert support not always available within an organization.
It’s the coordinated effort of these two components that tie the people element together.
Pillar #2 — Procedures
After people, we have Procedures. Mail screening SOP’s are critical in dealing with mail-borne threats.
They help set policy, set standards and training, establish screening processes, provide guidelines for suspicious item screening, and more.
For instance, if you have an executive protection program within your organization, your SOPs should be designed in a way that allows flexibility for the fluid nature of EP work.
This type of preparation helps maintain standards regardless of location or situation.

Pillar #3 — Training
Training is key when it comes to implementing mail screening and security procedures.
The idea here is that it needs to span all layers of the organization, it needs to educate, it needs to be measurable to confirm a level of understanding, and it needs to be continually updated and refreshed.
For example, training can be as simple as teaching folks the process and protocols for an emergency response or even something like conducting a tabletop exercise.
Either way, this should continue to be an ongoing process
Pillar #4 — Technology
As threats evolve and change, so does technology.
Increased technology brings increased false positives, which means you need to lean into humans and training as we have discussed.
If you are going to use technology, ensure you are using something that has a standard behind it much like the Safety Act highlighted here.
Pillar #5 — Response Plans
When it comes to response plans, the big takeaway is that you need to plan for the response you want to have.
If you do not have an emergency response plan in place, you should strongly consider getting one as soon as possible.
These documents mandate how a threat is managed and it also guides the actions of those involved. These plans need to be prepared and rehearsed often.
For example, your response plan should work through who you call and when. Note the differences in the two agencies on the slide.
Your situation, not a lack of preparation, should dictate who you call and when.
Mail Security Program Overview
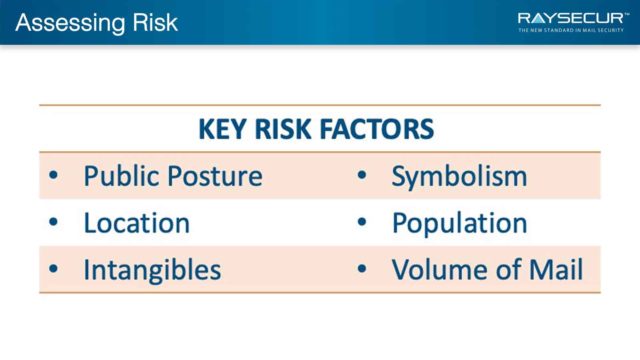
Assess your risk
A thorough risk assessment for each location will help ensure you implement the optimal policies, technologies, and procedures.
Correctly identifying the location’s risk as being low, medium, or high risk is a key component of filling your security gap.
Guidelines are based on:
- Site risk profile
- Physical layout of the facility
- Other unique requirements
Site-specific considerations:
- Internal mail transport routes
- Mailroom location and access
- Available technology
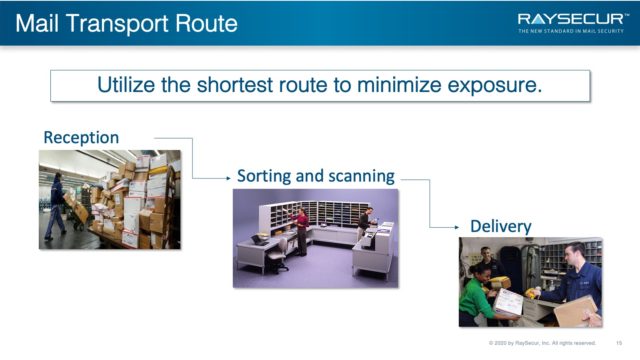
Shortest possible transport routes
To maintain efficiency and increase security, your internal mail transport route needs to be evaluated.
Your mail transportation starts with receipt of mail and continues until it arrives at the mail room and is screened and cleared.
If a dangerous item has been introduced to your organization by delivery, it is paramount that you minimize its exposure to people and property.
The shortest, most direct route is recommended.
Mail flow is an often-overlooked component of a mail security program. When done correctly, it is an important piece of contamination and exposure reduction strategies.
Mailroom location & access
Another component of implementing a mailroom security program is assessing the risk associated with your current mailroom location.
Be sure to evaluate certain aspects such as the location within the building and access control.
If a dangerous item is identified within the mailroom, what kind of impact will it have on operations? Who will be impacted?
Does the head of the organization have an office located immediately above the mailroom?
If so, and a mail threat would be discovered, what kind of concerns does that raise?
These are the types of questions to ask when assessing locations prior to implementation.
Review current procedures
One of the single biggest mail security improvements you can make is to centralize all of your mail handling.
A fragmented footprint not only allows for multiple entry points, but it also creates an environment where standards often vary from place to place.
Ideally, this site would be stand alone and have appropriate standoff from the main facility. However, this is not always possible and provisions need to be made to accommodate these scenarios.
1. Centralize all mail handling.
A fragmented footprint not only allows for multiple entry points but also creates an environment where standards often vary from place to place.
2. Locate the mail center in a stand-alone location, if possible.
Maintain appropriate standoff from the main facility. If it is not possible, provisions need to be made to accommodate these scenarios.
3. Assign a mailroom coordinator.
Often this is a full-time role within a company. But, if not, identify one person who oversees the above.
Additional considerations
- How is the mail processed?
- Is a visual inspection occurring at the area where mail is received?
- Is the mail then introduced to a more thorough visual and tactile inspection in the mailroom?
- Is technology available for more advanced screening?
- What are the roles of mailroom personnel?
- Do personnel know the key indicators of a suspicious mail piece?
- Do personnel know what emergency procedures to take to mitigate the various types of incidents they may be exposed to?
Standard Operating Procedures
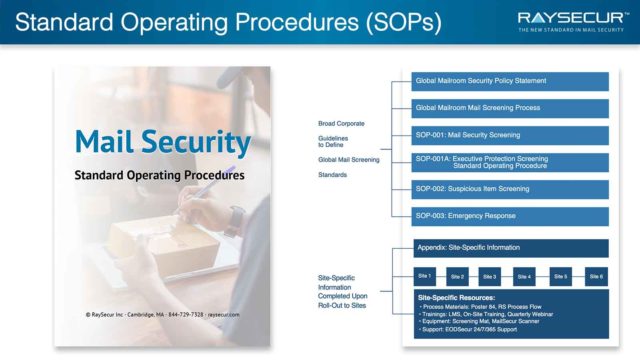
A major component of implementing a mailroom security program is to integrate robust standard operating procedures (SOP’s).
When these are established, all personnel will understand their role and responsibilities within the mail security program.
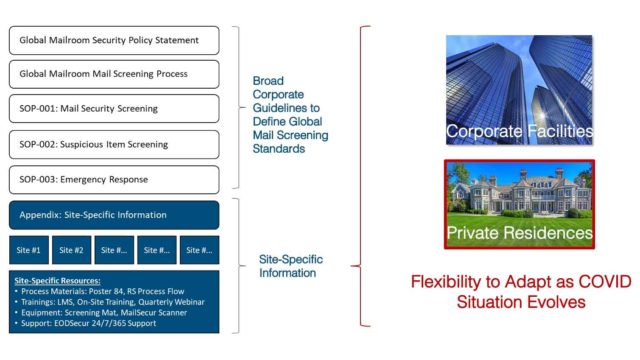
Mail security SOP’s should include:
- Global Mailroom Security Policy Statement
- Global Mailroom Mail Screening Process
- Mail Security Screening Procedure
- Suspicious Item Screening Procedure
- Emergency Response Procedure
Well-trained personnel
Having well trained personnel is key to mitigating mail-borne threats.
Not only will efficiency increase, but an experienced mail screener is more likely to see something out of the norm.
They are also able to more easily recognize trusted senders to expedite screening and have a better understanding of emergency procedures.
At a minimum, all mail handlers should be trained in the fundamentals of mail security covering the types of mail threats, identification of suspicious items, and the basics of visual and tactile inspection.
Operators of mail security screening technology should be trained in all aspects of their particular screening technology operation and threat detection.
Securing your facility
The final step in implementation of a mailroom screening program is bringing everything together.
At this point you will have conducted a risk analysis, reviewed current policies and procedures, integrated standardized operating procedures, and trained your personnel.
Reinforce this work by offering personnel continuing education, training, and expanded understanding of why their work is important.
Take a proactive role in developing a security-first mindset that works from the top down.
When front-line personnel see upper management engaged in the security process, they are more likely to buy in to the importance of their role.
Additional Resources
US & UK Guidelines
RaySecur recommends mailroom and security personnel review the guide put out by US DHS, Best Practices for Safe Mail Handling.
The DHS guide discusses risk assessment of the facilities and mail handling operations, and best practice to minimize risk and exposure to personnel and the public.
For further documentation, the UK CPNI Guidelines, known as PAS 97, are an excellent resource.
The PAS 97 specifies measures to assist businesses and other organizations in identifying and minimizing the impact of items of mail that represent a threat, or could otherwise cause concern or disruption.
Classification & requirements
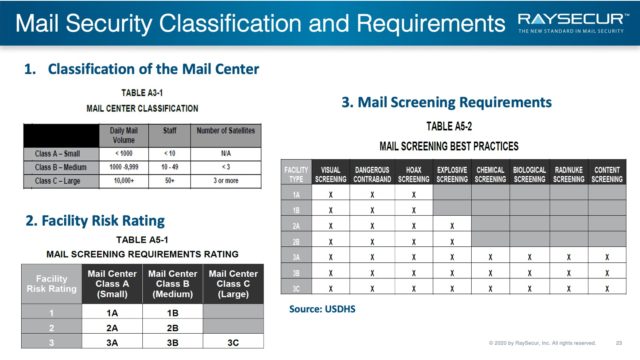
The US DHS provides several helpful tables to help organization rate their own risk, and begin to plan their mail security protocols.
Size & scope
Table A3-1 will help determine the size of your mail center, in relation to other organizations’ mail centers.
Facility risk level
As seen in previous slides, organizations can be rated high risk 1, medium 2, or low risk 3.
By cross referencing the size of center A,B,C with level of risk 1,2,3 will give you the requirement rating, found in table A5-1.
What to screen for
Table A5-2 will provide a guide to help determine what your facility should screen for.
This is an excellent guide to start discussing with your team how to best implement a mail center security process.
Safe mail handling
This slide highlights a few resources organizations should reference during mail security program implementation.
The first is Poster 84, which annotates common characteristics to look for in relation to suspicious mail or packages.
The second is the guide put out by DHS, Best Practices for Safe Mail Handling.
What’s next?
Implementing a mail security program is often the missing link in a comprehensive physical security program.
It is unfamiliar to many and may present challenges to those who are new to the world of mail security.
RaySecur can help implement a sound mail center security practice and bridge the gap in your facility’s physical security.