In this presentation, RaySecur’s Director of Mail Security explains how to assess your mail security risk and develop SOPs for mail screening.
Mail screening SOPs define roles and responsibilities within the mail security program for all personnel.
Implementing a mail security program is often the missing piece in a comprehensive physical security program.
Download the PDF & Files ↓

Will Plummer
Chief Security Officer
& EODSecur Program Director
Will is 25-year veteran of the US Army, where he earned a Bronze Star with Valor as a Master Explosive Ordnance Disposal (EOD) Technician.
- Commanded multiple Special Ops units with multiple combat deployments
- Certified Multifunctional Logistician
- Supported Civil Authorities on Hundreds of Full-Spectrum EOD incidents
- Directed VIP support for the last 8 U.S. Presidents

Cody Martin
Director of Mail Security
& SOP Team Lead
Cody Martin had over 12 years of experience as a Federal Agent with the U.S. Postal Inspection Service, and several additional years as a mail security consultant.
- USPIS Dangerous Mail Specialist & Instructor
- Co-created USPIS IED Program for National Headquarters
- Investigator on high-profile / VIP cases
- Screened mail for the NFL, NBA, President George W. Bush (ret.)
- First responder to hundreds of incidents
Mail Security Risk Assessment
This outline provides a general overview of the major building-blocks which constitute a comprehensive Mail Security Program.
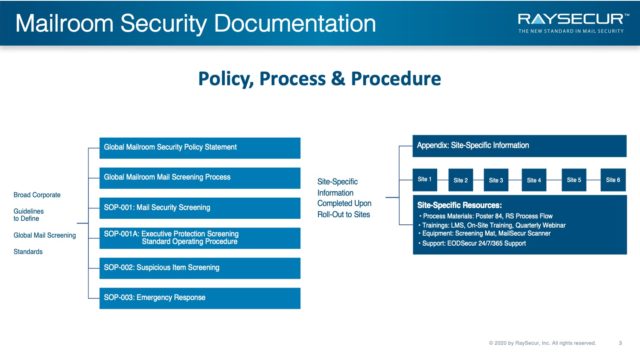
Policy, Process & Procedure
Mail Security SOP documentation is structured to encompass global corporate-level standards that apply across the board. However, there may be site-specific requirements that must be considered.
At a minimum, all sites are expected to adhere to the global mail screening standards, and site-specific guidelines may be considered in addition to standards that apply globally.
Site specific guidelines are based on the site’s risk profile, the physical layout of the facility, and any other unique requirements.
DHS High-Risk Industries & Other Factors
The Department of Homeland Security and Interagency Security Committee identify some of the risk factors for mail-borne threats.
About a dozen industries are considered high risk, and are more likely to receive threats:
- Banking
- Energy
- Power
- Defense
- Legal
- Pharmaceutical
- Chemical
- Nuclear Facilities
- Transportation (Air, Sea, Land)
- Construction
- Health and Medical
- Telecommunications
- Bio-Medical Research
- Any organization considered part of the “Military Industrial Complex”
Symbolism
A well-known or well-publicized entity is at risk, by nature of their notoriety. This often includes brands that promote controversial items or have overlap with politically-charged subjects.
An attack on one organization of a certain type could have “downstream” affects on the whole industry.
Think of USPS after the anthrax mail-borne attacks.
Location
Organizations in large, multi-tenant facilities and urban centers are at higher risk.
This especially true for organizations in symbolic areas: Washington DC and New York City, for example.
Size & Population
Organizations with large employee populations are at higher risk.
The same is true for organizations located in areas with a high-density population—this can increase risk, regardless of the number of their employees.
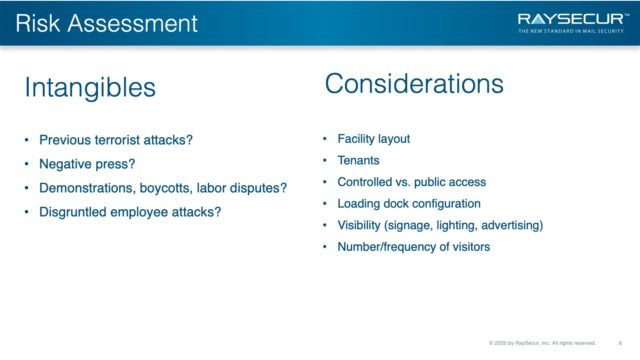
Intangibles & Other Considerations
A wide range of additional factors must be considered when evaluating an organization’s and facility’s risk profile, some of which are organization or industry specific.
For example:
- Has the organization/tenants, or the area within the industrial sector, been the target of any previous terrorist attacks?
- Has the organization/tenants been the subject of any highly publicized negative press?
- Has the organization/tenants been the target of organized demonstrations, boycotts, labor disputes, etc.?
- Has the organization/tenants been the subject of attacks by disgruntled employees?
An affirmative answer to any questions such as these should be considered in the risk assessment.
Other aspects that should be considered include, but are not limited to, such factors as:
- Facility layout–single building, multiple buildings, or campus;
- Single tenant or multiple tenants;
- Controlled access, public access, or a combination; Loading dock configuration;
- Visibility of the organization’s facility that contains the mail center (e.g., signage, lighting, advertising); and
- Number and frequency of visitors and/or tourists to the facility and the area in which it is located.
DHS Assessment Worksheet
On page 40 of their Mail Screening Best Practices guide, the US DHS provides a mail center assessment worksheet.
The worksheet provides an easy way for mail and security personnel to assess their facilities’ level of risk.
- Buildings & Location
- # of Floors & Mail stops
- General Office Security
- General Mail Security
- Employee Identification & Training
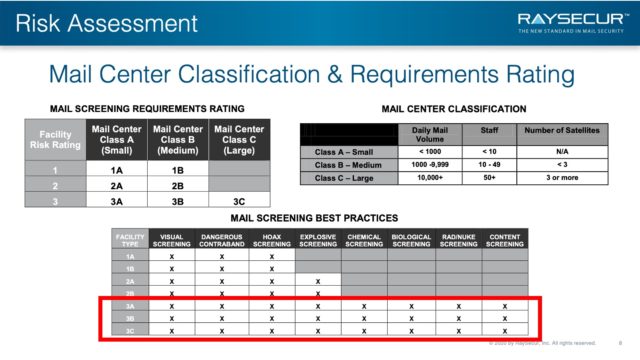
Classification & Requirements Rating
These tables, again drawn from the DHS Mail Screening Best Practices guide, provide recommendations for an exact risk analysis, using DHS criteria.
| Daily Mail Volume | Staff | Number of Satellites | |
|---|---|---|---|
| Class A — Small | < 1000 | < 10 | N/A |
| Class B — Medium | 1000 – 9,999 | 10 – 49 | < 3 |
| Class C — Large | 10,000+ | 50+ | 3 or more |
| Facility Risk Rating | Mail Center Class A (Small) | Mail Center Class B (Medium) | Mail Center Class C (Large) |
|---|---|---|---|
| 1 | 1A | 1B | |
| 2 | 2A | 2B | |
| 3 | 3A | 3B | 3C |
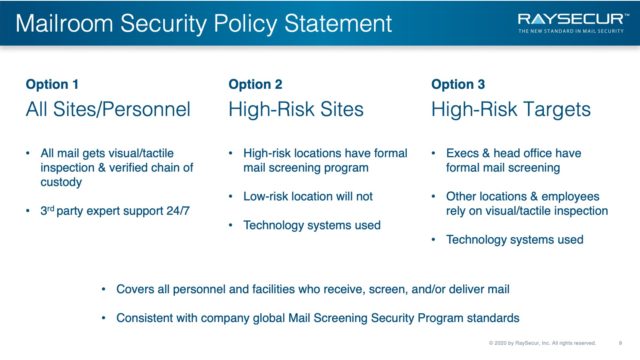
Mailroom Security Policy Statement Options
Choose the option that will most resemble your desired policy, and expand on it. This will create a framework to use as you work through the building blocks.
Be sure to keep your site’s risk levels in mind as they relate to your policy statement.
Option 1: All Sites/Personnel
- All mail gets visual/tactile inspection & verified chain of custody
- 3rd party expert support 24/7
Option 2: High-Risk Sites
- High-risk locations have formal mail screening program
- Low-risk location will not
- Technology systems used
Option 3: High-Risk Targets
- Execs & head office have formal mail screening
- Other locations & employees rely on visual/tactile inspection
- Technology systems used
All SOP Options:
- Covers all personnel and facilities who receive, screen, and/or deliver mail
- Consistent with company global Mail Screening Security Program standards
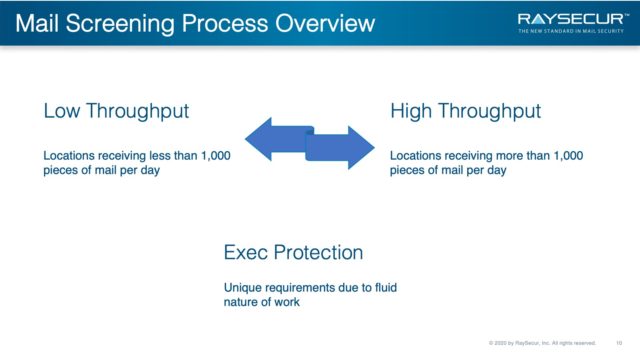
Mail Screening Process Overview
In general, mail screening process requirements are based on the volume of mail received by a particular facility or location per day or by unique requirements related to protectees:
- Low Throughput: Locations receiving less than 1,000 pieces of mail per day
- High Throughput: Locations receiving more than 1,000 pieces of mail per day
- Executive Protection: Unique requirements due to fluid nature of work
Regardless of the classification, mail security processes share several critical and fundamental screening steps, namely: visual screening, verification of the chain of custody, and technology screening.
The processes differ only in the routing of particular workflows to achieve the same goal – safe, effective, and efficient mail security.
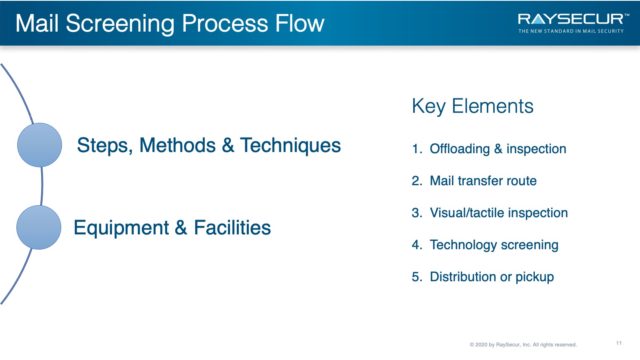
Mail Screening Process Flow
The Mail Screening Process Flow describes a sequence of steps, methods, techniques, and related equipment and facilities, which together form the basis of a global corporate standardized mail screening process.
Regardless of the site or specific process flow, the following key elements are broadly applicable to the process flows described previously:
- Initial offloading and baseline inspection.
- Mail transfer route.
- Subsequent visual and tactile inspection and technology screening of the mail in the mail screening area.
- Distribution or customer pickup.
SOP-001: Enhanced Security Mail Screening
The purpose of this SOP is to define and outline safe and approved enhanced mail security screening procedures that serve as standards for the organization to follow.
This SOP is covered in four sections critical to maintaining a high level of mail security for the organization: receiving area, transfer route, mailroom operation, and delivery.
Definition of Key Threat Indicators
For reference, below is a list that is not all-inclusive, but provides several examples meant to inform the mailroom employee of the type of threats to look for.
- Items that should be light are often excessively heavy, lopsided, or simply do not match what they should be.
- Oil stains, smells, or signs of chemical reactions are not normal.
- Excessive postage is abnormal and is a key identifier of something questionable.
- Often the “addressee” is general and to an individual’s job or title and not the person holding it.
- Items marked with Restrictive markings like PRIVATE, FRAGILE, or URGENT.
- Attempts to obscure identification of the sender such as block writing.
- Package has exposed wires, wrapped in string, or excessive tape to ensure the difficult removal of items.
- Previous postmark cancellation, duplicate sender and return address, or insults within the writing.
Implementation of Enhanced Mail Security Screening
The following four sections cover critical aspects of the screening process required to maintain a high level of mail security for the organization, including the mail receiving area, transfer route, mailroom operation, and delivery.
Section I: Receiving area
- Centralize when possible
- Initial visual screening
- Ready for transfer
Section II: Transfer Route
- Travel minimum distance
- Reduce any possible contamination
- Consider time of day, number of personnel, critical infrastructure, etc.
SOP-001A: Executive Protection Mail Screening
The purpose of this standard operating procedure (SOP) is to define and outline safe and approved enhanced mail security screening procedures that serve as standards for the organization to follow.
This SOP is covered in four sections critical to maintaining a high level of mail security for the organization: receiving area, transfer route, mailroom operation, and delivery.
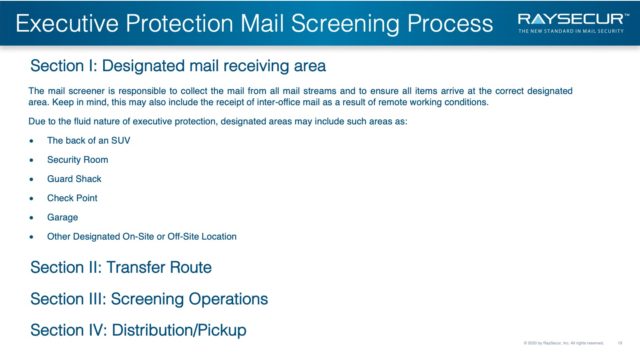
Section I: Designated Mail Receiving Area
The mail screener is responsible to collect the mail from all mail streams and to ensure all items arrive at the correct designated area. Keep in mind, this may also include the receipt of inter-office mail as a result of remote working conditions.
Due to the fluid nature of executive protection, designated areas may include such areas as:
- Back of an SUV
- Security Room
- Guard Shack
- Check Point
- Garage
- Other designated on- or off-site location
SOP-002: Suspicious Package Screening
The purpose of this standard operating procedure (SOP) is to outline the procedure to follow if a suspicious item is detected.
This document defines the procedures to be followed by all global sites in accordance, regardless of available screening technologies on site.
Suspicious Package Screening
Section I: How to Validate a Suspicious Item
- Use best judgment, intuition, and attention to detail.
- In general, an item such as USPS Poster 84 can a constant reminder of key indicators and examples of typical threats.
- Use suspicious characteristics mentioned above as a basis.
- Can you confirm the package as legitimate via addressee or sender?
Section II: How to Render a Situation Safer
- If an item is deemed suspicious, the mail handler will assess the best way to reduce the risk to people and infrastructure.
- The mail screener is expected to place the suspicious item down to ensure no one else is exposed to the situation.
Section III: How to De-escalate the Situation
- In this step, the mail screener will reach out for support either via corporate security or the SME’s.
- Mail screener should follow the steps on the emergency response card. (call support, provide relevant information from the package)
Section IV: How to escalate to an emergency response
- Additional review will be conducted with internal or external support
- If the item cannot be rendered safe, corporate security will advise ERP to be initiated.
SOP-003: Emergency Response
The purpose of this standard operating procedure (SOP) is to outline the process for initiating an emergency response.
This document defines the procedures for all global sites to follow in accordance with the corporate standards.
The mail processor in conjunction with the local security team and/or the third-party subject matter expert have determined that the mail item cannot be properly rendered safe and an emergency response is required.
Scope
This procedure outlines the basic steps and processes to follow in the initiation of an emergency response. This SOP covers several key processes, namely:
I. communicating the threat to the internal security team,
II. mitigating the risk to employees and facilities, and
III. requesting the help of the first responders.
Implementation
Initiating the emergency response plan consists of completing the following steps.
- Evacuation
- Communicating the Threat to the Security Team
- Risk Mitigation
- Calling First Responders
Step 1: Evacuation
- If at any time, a person is physically reacting to the mail piece, or if the mail piece is emitting smoke, vapors, fumes, or any other potentially threatening substance, initiate your emergency plan and evacuate the area.
- If not, proceed through the following steps of the emergency response plan process
Step 2: Communicating the Threat to the Security Team
- At this point, the appropriate person will reach out through the chain of command identified on an emergency response card.
- Relay all pertinent data about the threat. Be prepared to discuss why the suspicious package could not be rendered safe.
- The final decision on making a call to the first responder is the responsibility of the highest-ranking security officer, or his/her designee if not available.
Step 3: Risk Mitigation
- In this step, a good-faith effort by the mail screener and site security are put in place to reduce risk and minimize exposure to employees and facilities.
Step 4: Calling First Responders
- A call will be made to first responders such as the local hazmat team, fire department, police, US Postal Inspection Service, or any applicable jurisdiction.
Additional Resources
Emergency Response SOP
USPS Poster 84 annotates common characteristics to look for in relation to suspicious mail or packages.
RaySecur’s sample Emergency Response Card makes it easy for mailroom staff to alert the proper parties in the event of an emergency.
US DHS & UK CPNI Guidelines
RaySecur recommends mailroom and security personnel review the guide put out by US DHS, Best Practices for Safe Mail Handling.
The DHS guide discusses risk assessment of the facilities and mail handling operations, and best practice to minimize risk and exposure to personnel and the public.
For further documentation, the UK CPNI Guidelines, known as PAS 97, are an excellent resource.
The PAS 97 specifies measures to assist businesses and other organizations in identifying and minimizing the impact of items of mail that represent a threat, or could otherwise cause concern or disruption.
Custom SOPs for your Company
RaySecur offers private, 1-on-1 workshops, led by Director of Mail Security, Cody Martin.
Cody and the Mail Security team cover mail security in detail, and help organizations assess their level of risk, and plan their mail security SOPs.
Attendees will receive:
- Complete SOP Policy Statement
- Framework of a mail security SOP
- Documentation of risk level & mail threats
Mail safety SOPs define roles and responsibilities within the mail security program for all personnel.
Implementing a mail security program is often the missing piece in a comprehensive physical security program.